Midterm
CS 246
Spring 2016
Due: March 17, 2016
Frequently asked Questions, FAQ
The following three problems involve using OpenCV to manipulate an
image. Each problem is worth 40 points. Your submission should include
all source files, a single Makefile that can make all of the problems
by calling make on its own, and any supporting png or txt files needed
to test the programs. In addition, there should be a README that
describes how each of your programs works, and if there are any issues
that we should know about. Your submission should be in the form of a
mercurial repository in a directory called midterm in your username
course directory.
Resources: For this project you may use the OpenCV API and
OpenCV tutorials, but no other web sources. Each time you look at a
resource, you should put a comment in your code with the URL or the
page of the book that you use.
Work from home:
If you don't have X11, then you can do most of your work locally, keep
your code synchronized using mercurial, and compile and run remotely.
This
Document is a step by step guide for doing this starting with
creating your repository in your course directory. Additional links
and programs are mentioned below.
|
Windows
how to.
|
|
Mac
X11 client.
|
|
ssh -Y username@powerpuff.cs.brynmawr.edu
|
|
Programs (on powerpuff):
|
|
imlib2_view beyisbae.png
|
|
gimp beyisbae.png
|
|
convert -resize WWWxHHH\! src.type1 dst.type2 |
where type1 and type2 can be jpg,png, etc., src and dst are
filenames,
WWW is a number of pixels wide, HHH is number of
pixels high
\! is to force a change in aspect ratio
|
|
emacs
|
Problem 1.
Image Steganography. Use the beyisbae.png image from
/rd/cs246s2016/shared/midterm/beyisbae.png as a carrier image for a
hidden message. Create an encode program that reads a text file (or
stdin until you type ctrl-d), and puts the contents into the image
data array in a way that is recoverable by a decode program, and then
writes the image as "secretMessage.png". Write the
decode program that reads in the secretMessage.png (and if necessary
beyisbae.png) file, and then prints the secret message to the console
as text. Extra credit will be given to solutions where it is harder to
detect visually that the image has a secret message.
Problem 2.
Create a set of at least 3, and at most 5, different sized 2-d
filters. The filters should have some similar characteristics, but be
different based on size (e.g. 3 x 3 vs. 7 x 7) or amplitude (i.e. the
magnitude of the values in your filter). Apply the
filters in at most 10 different ways on the beyisbae.png and any other
png file that you would like to filter. Your filters must be of your
own design, and not based on a filter that you've seen before or that
is well known. Save the results of each time you filter the image, and
put the filter application order in the readme file when describing
the application of the filters. Your filters should be in a source file
with an appropriate name stored as initialized Mat objects, and you
should be able to call each one by a name to apply it to a
filter. You may use a class for this, but it is not required. Your
program for problem 2 should use this file to apply the filters on the
images as described above.
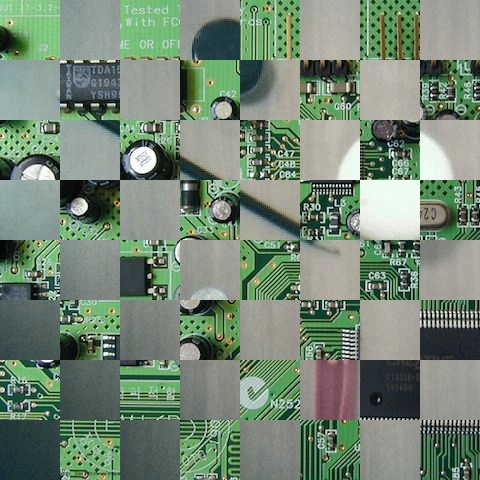
Problem 3
FancyBoard, write a program that takes 2 images and creates a square
checkers board using the shortest side of the images as the side
length of the square board. The
squares of the board should alternate between the data of one image
and the data of
other. The program should ask the user for the name of each image file
to use as input, and the name of the output file, each separated by
whitespace.
The squares can consist of a miniature version of the corresponding
image, or, for more points, it should consist of the pixel values at
the part of the corresponding image. Extra credit if you do both and
create an option to choose which version.
Example:
Image A:

Image B:

Miniature Board:

Pixel Values Board:
Frequently asked Questions, FAQ
Question 1: What exactly gets us full credit on problem 1?
Verbose Question: Problem 1 states: "Write the decode program that reads in the
secretMessage.png (and if necessary beyisbae.png) file, and then
prints the secret message to the console as text. Extra credit will be
given to solutions where it is harder to detect visually that the
image has a secret message." This indicates that the bare minimum of
just replacing pixels is the 100%, and making it harder to detect was
merely fluff. But in class, you indicated otherwise, and made it sound
like what the problem states as "extra credit" was full credit. Which
is it?
Answer 1: If you do the bare minimum described in class,
then it will corrupt the image to the point that you can't tell what
the image is, so you wouldn't get full credit. In order to get full
credit, you need to still be able to see the original image even if
there are some occasional bad pixels. If you can visibly see a lot of
bad pixels, but the image is still identifiable, then you would get full
credit, but it is still very
easy to detect that there is a secret image,so you wouldn't get extra credit.
Question 2: Can you clarify the statement from problem 2:
"you should be able to call each one by a name to apply it to a
filter".
Verbose Question: Is it okay to have a function that uses the name to return a Mat value or does it need to specifically use the name to call the filter function? Or something else entirely?
Answer 2: The full sentence for the quoted text is: "Your
filters should be in a source file with an appropriate name stored as
initialized Mat objects, and you should be able to call each one by a
name to apply it to a filter."
You can implement the named Mat in
a number of ways. For instance: - You can write a function with a particular name that returns the Mat that is the filter.
- You could have a global static Mat with a particular name.
- You could have a filter that takes a name as a string and returns the Mat.
- There are probably other ways to do it as well.
Last modified: Wed Mar 16 00:18:12 EDT 2016



